- > > >
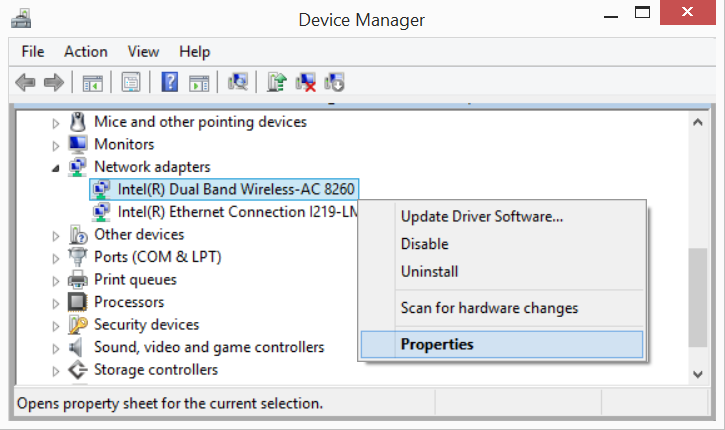
Although, for the most part, setting up a wired network connection on a Windows 10 device is as easy as plugging in an Ethernet cable, connecting using a wireless adapter requires some additional. Routers – A router is a device like a switch that routes data packets based on their IP addresses. Router is mainly a Network Layer device. Routers normally connect LANs and WANs together and have a dynamically updating routing table based on which they make decisions on routing the data packets.
Data Acquisition Categories

Software
Program
Amplifiers
Wireless fidelity, also know as WiFi, is a term used to describe wireless networking technology. Instead of using cables to move data through an Ethernet network, WiFi uses radio waves, eliminating the need for a physical connection to send and receive data. This allows multiple users to connect to the internet, a local area network or any other WiFi enabled product without the limitations of being tethered to a CAT-5 Ethernet cable.
The IEEE (Institute of Electrical and Electronic Engineers) has set three standards in the area of wireless technology; 802.11a, 802.11b and 802.11g (with a fourth 802.11n high speed standard pending). These standards relate primarily to speed (data transfer rates), frequency and range.
Click on the chart for a closer look. Chart courtesy of Linksys
By now you're probably wondering what this has to do with data acquisition. Although WiFi devices are used primarily as wireless Internet or LAN access points, their applications are far ranging. A WiFi network can be used to access a DATAQ Instruments' Ethernet device from up to 150 feet away! WiFi capability allows you to monitor your WinDaq data from virtually anywhere in the building without the bother of running back and fourth or laying cable, all for around $150.
All you need to begin wireless data acquisition. A. Wireless Router; B. Wireless Access point; and C. DATAQ Instruments DI-730EN (or any DATAQ Instruments Ethernet device). We used wireless products manufactured by D-Link for our test. Other leading WiFi manufacturers include Linksys and Netgear.
Setting Up Your Wireless Data Acquisition Network
For our test we used a DATAQ Instruments DI-730EN along with a D-link 802.11g DI-634M Wireless Broadband Router and a D-link DWL-2100AP Wireless Access Point.
The router was connected to a Dell Dimension desktop computer with a 2.53GHz Intel Celeron D processor. Four tests were conducted. The wireless access point was first placed approx. 10 feet away, in the same room as the router and then 60 feet away, in a 3 second room (transmitting through two walls constructed of metal studs and drywall). The maximum record to disk rate without gaps, using WinDaq software, was 170,000 samples per second at 10 feet and 120,000 samples per second at 60 feet (at standard 802.11g, 54Mbps transfer rates). Using D-Link's Super G Turbo technology to boost communication speeds even further (108Mbps), we were able to achieve gap free record to disk rates as high as 186,046 samples per second at 10 feet and 155,000 samples per second at 60 feet.
| 10 feet | 60 feet | |
| Standard G | 170,000 S/s | 120,000 S/s |
| Super G Turbo Technology | 186,046 S/s | 155,000 S/s |
| Gap free record to disk rates at standard 802.11g and Super G Turbo communication speeds. | ||
Setup was a simple, four step process:
- Connect port one of the D-Link Wireless Router to the Ethernet card of your computer using a CAT-5 patch cable.
- Connect the D-Link Bridge to the DI-730EN using a CAT-5 patch cable.
- Run the D-Link configuration utility and install software for the wireless router.
- Power up the DI-730EN and run WinDaq software as you normally would.
That's all there is to it! In a matter of minutes you can be up and running at sample rates as high as 186,000 samples per second with little or no help from your network administrator. So take a few minutes out of your day, set it up, and enjoy the convenience of wireless data acquisition.
Real Life Application—The University of Akron
To further illustrate the capabilities of wireless data acquisition, we'll take a look at one such wireless network being used by The University of Akron in Akron, Ohio. As part of The Society of Automotive Engineers, a group of engineering students at The University of Akron take part in a project that requires them to design and fabricate small formula-style cars. These cars are then entered into a national competition against designs from other schools and judged based upon design and performance.
One of the cars designed and built by engineering students at The University of Akron (click on photo for enlarged view).
To optimize the performance of their cars, students at The University of Akron use wireless data acquisition technology to monitor on-board data while the cars are on the track. For example, one such measurement is shock absorber travel, measured using linear potentiometers. This data is collected using a DATAQ Instruments DI-720EN and is then transmitted via an SMC Networks wireless access point to a laptop computer. The data is then reviewed and analyzed using WinDaq software. The students are able to receive and record their data (at a sample rate of 100 cycles per second × 5 channels) from up to 1000 feet away in the open, outdoor environment with the aid of a parabolic WiFi dish antenna. Stmicroelectronics port devices driver download. Virtually any measurement, from engine temperature to fuel level, can be received and recorded in real time.
Rear view of a DATAQ Instruments DI-720EN mounted inside one of the cars (left) and the SMC wireless access point mounted atop the engine (right). Click on photos for enlarged view.
The data collected using wireless data acquisition technology can prove invaluable to the engineering students when it comes to making adjustments to improve the performance of their cars. Rather than the driver sensing a problem and making a hit or miss adjustment to correct it, precise adjustments can be make based on the real-time track data.This is just one example of the cost effective power and convenience of wireless data acquisition.
This tutorial explains Wireless Network types (WLANS, WPANS, WMANS and WWANS) and Wireless network terminology (Ad hoc mode, Infrastructure mode, BSS, ESS, BSA, SSID, WEP, EAP, WPA, WPA2, Infrared, Bluetooth, FHSS, DSSS, FHSS, OFDM, MIMO, RF, Omni directional, 802.11g, 802.11a and 802.11h ) in detail.
A wireless network enables people to communicate and access applications and information without wires. This provides freedom of movement and the ability to extend applications to different parts of a building, city, or nearly anywhere in the world. Wireless networks allow people to interact with e-mail or browse the Internet from a location that they prefer.
Many types of wireless communication systems exist, but a distinguishing attribute of a wireless network is that communication takes place between computer devices. These devices include personal digital assistants (PDAs), laptops, personal computers (PCs), servers, and printers. Computer devices have processors, memory, and a means of interfacing with a particular type of network. Traditional cell phones don't fall within the definition of a computer device; however, newer phones and even audio headsets are beginning to incorporate computing power and network adapters. Eventually, most electronics will offer wireless network connections.
As with networks based on wire, or optical fiber, wireless networks convey information between computer devices. The information can take the form of e-mail messages, web pages, database records, streaming video or voice. In most cases, wireless networks transfer data, such as e-mail messages and files, but advancements in the performance of wireless networks is enabling support for video and voice communications as well.
Types of Wireless Networks
WLANS: Wireless Local Area Networks
WLANS allow users in a local area, such as a university campus or library, to form a network or gain access to the internet. A temporary network can be formed by a small number of users without the need of an access point; given that they do not need access to network resources.
WPANS: Wireless Personal Area Networks
The two current technologies for wireless personal area networks are Infra Red (IR) and Bluetooth (IEEE 802.15). These will allow the connectivity of personal devices within an area of about 30 feet. However, IR requires a direct line of site and the range is less.
WMANS: Wireless Metropolitan Area Networks
This technology allows the connection of multiple networks in a metropolitan area such as different buildings in a city, which can be an alternative or backup to laying copper or fiber cabling.
WWANS: Wireless Wide Area Networks
These types of networks can be maintained over large areas, such as cities or countries, via multiple satellite systems or antenna sites looked after by an ISP. These types of systems are referred to as 2G (2nd Generation) systems.
Comparison of Wireless Network Types
| Type | Coverage | Performance | Standards | Applications |
Wireless PAN | Within reach of a person | Moderate | Wireless PAN Within reach of a person Moderate Bluetooth, IEEE 802.15, and IrDa Cable replacement for peripherals | Cable replacement for peripherals |
Wireless LAN | Within a building or campus | High | IEEE 802.11, Wi-Fi, and HiperLAN | Mobile extension of wired networks |
Wireless MAN | Within a city | High | Proprietary, IEEE 802.16, and WIMAX | Fixed wireless between homes and businesses and the Internet |
Wireless WAN | Worldwide | Low | CDPD and Cellular 2G, 2.5G, and 3G | Mobile access to the Internet from outdoor areas |
Wireless Networking
Wireless networking is the new face of networking. Wireless networking have been around for many years. Cell phones are also a type of wireless communication and are popular today for people talking to each other worldwide.
Wireless networking are not only less expensive than more traditional wired networking but also much easier to install. An important goal of this site is to provide you adequate knowledge for installing a wireless network and get certified in wireless networks as well as.
Perhaps you already useing wireless networking in your local coffee shop, at the airport, or in hotel lobbies, and you want to set up a small office or home network. You already know how great wireless networking is, so you want to enjoy the benefits where you live and work. It is truly transformational to one's lifestyle to decouple computing from the wires! If you are looking to set up a wireless network, you've come to the right place. We will show you the best way to set up wirless network easily. Many people are looking to find out how to use wireless networking at home.
In this wireless networking section we provides An Absolute Beginner's Guide in the perfect format for easily learning what you need to know to get up to speed with wireless network without wasting a lot of time.
The organization of this site, and the special elements that we have described in this section will help you get the information you need quickly, accurately, and with clarity. In this section you will find inspiration as well as practical information. we believe that Wireless networks is a modest technology that has the power to have a huge and positive impact. This is wonderful material, and it's lots of fun! So what are you waiting for? It's time to Go for wireless networking.
Wireless Basic
Radio Frequency Transmission Factors
Radio frequencies (RF) are generated by antennas that propagate the waves into the air.
Antennas fall under two different categories:
directional and omni-directional.

Directional antennas are commonly used in point-to-point configurations (connecting two distant buildings), and sometimes point-to-multipoint (connecting two WLANs).
An example of a directional antenna is a Yagi antenna: this antenna allows you to adjust the direction and focus of the signal to intensify your range/reach.
Omni-directional antennas are used in point-to-multipoint configurations, where they distribute the wireless signal to other computers or devices in your WLAN. An access point would use an omni-directional antenna. These antennas can also be used for point-to-point connections, but they lack the distance that directional antennas supply
Three main factors influence signal distortion:
- Absorption Objects that absorb the RF waves, such as walls, ceilings, and floors
- Scattering Objects that disperse the RF waves, such as rough plaster on a wall, carpet on the floor, or drop-down ceiling tiles
- Reflection Objects that reflect the RF waves, such as metal and glass
Responsible body
The International Telecommunication Union-Radio Communication Sector (ITU-R) is responsible for managing the radio frequency (RF) spectrum and satellite orbits for wireless communications: its main purpose is to provide for cooperation and coexistence of standards and implementations across country boundaries.
Two standards bodies are primarily responsible for implementing WLANs:
- IEEE defines the mechanical process of how WLANs are implemented in the 802.11 standards so that vendors can create compatible products.
- The Wi-Fi Alliancebasically certifies companies by ensuring that their products follow the 802.11 standards, thus allowing customers to buy WLAN products from different vendors without having to be concerned about any compatibility issues.
Frequencies bands:
WLANs use three unlicensed bands:
- 900 MHz Used by older cordless phones
- 2.4 GHz Used by newer cordless phones, WLANs, Bluetooth, microwaves, and other devices
- 5 GHz Used by the newest models of cordless phones and WLAN devices
- 900 MHz and 2.4 GHz frequencies are referred to as the Industrial, Scientific, and Medical (ISM) bands.
- 5 GHz frequency the Unlicensed National Information Infrastructure (UNII) band.
- Unlicensed bands are still regulated by governments, which might define restrictions in their usage.
A hertz (Hz) is a unit of frequency that measures the change in a state or cycle in a wave (sound or radio) or alternating current (electricity) during 1 second.
Transmission Method
Direct Sequence Spread Spectrum (DSSS) uses one channel to send data across all frequencies within that channel. Complementary Code Keying (CCK) is a method for encoding transmissions for higher data rates, such as 5.5 and 11 Mbps, but it still allows backward compatibility with the original 802.11 standard, which supports only 1 and 2 Mbps speeds. 802.11b and 802.11g support this transmission method.
OFDM (Orthogonal Frequency Division Multiplexing) increases data rates by using a spread spectrum: modulation. 802.11a and 802.11g support this transmission method.
MIMO (Multiple Input Multiple Output) transmission, which uses DSSS and/or OFDM by spreading its signal across 14 overlapping channels at 5 MHz intervals. 802.11n uses it. Use of 802.11n requires multiple antennas.
WLAN Standards
| Standards | 802.11a | 802.11b | 802.11g | 802.11n |
| Data Rate | 54 Mbps | 11 Mbps | 54 Mbps | 248 Mbps (with 2×2 antennas) |
| Throughput | 23 Mbps | 4.3 Mbps | 19 Mbps | 74 Mbps |
| Frequency | 5 GHz | 2.4 GHz | 2.4 GHz | 2.4 and/or 5 GHz |
| Compatibility | None | With 802.11g and the original 802.11 | With 802.11b | 802.11a, b, and g |
| Range (meters) | 35–120 | 38–140 | 38–140 | 70–250 |
| Number of Channels | 3 | Up to 23 | 3 | 14 |
| Transmission | OFDM | DSSS | DSSS/OFDM | MIMO |
Two 802.11 access modes can be used in a WLAN:

- Ad hoc mode
- Infrastructure mode
Ad hoc mode is based on the Independent Basic Service Set (IBSS). In IBSS, clients can set up connections directly to other clients without an intermediate AP. This allows you to set up peer-to-peer network connections and is sometimes used in a SOHO. The main problem with ad hoc mode is that it is difficult to secure since each device you need to connect to will require authentication. This problem, in turn, creates scalability issues.
Infrastructure mode was designed to deal with security and scalability issues. In infrastructure mode, wireless clients can communicate with each other, albeit via an AP. Two infrastructure mode implementations are in use:
- Basic Service Set (BSS)
- Extended Service Set (ESS)
In BSS mode, clients connect to an AP, which allows them to communicate with other clients or LANbased resources. The WLAN is identified by a single SSID; however, each AP requires a unique ID, called a Basic Service Set Identifier (BSSID), which is the MAC address of the AP’s wireless card. This mode is commonly used for wireless clients that don’t roam, such as PCs.
In ESS mode, two or more BSSs are interconnected to allow for larger roaming distances. To make this as transparent as possible to the clients, such as PDAs, laptops, or mobile phones, a single SSID is used among all of the APs. Each AP, however, will have a unique BSSID.
Coverage Areas
A WLAN coverage area includes the physical area in which the RF signal can be sent and received Two types of WLAN coverage’s are based on the two infrastructure mode implementations:
- Basic Service Area (BSA)
- Extended Service Area (ESA)
The terms BSS and BSA, and ESS and ESA, can be confusing. BSS and ESS refer to the building topology whereas BSA and ESA refer to the actual signal coverage
BSA With BSA, a single area called a cell is used to provide coverage for the WLAN clients and AP
ESA With ESA, multiple cells are used to provide for additional coverage over larger distances or to overcome areas that have or signal interference or degradation. When using ESA, remember that each cell should use a different radio channel.
How an end user client with a WLAN NIC accesses a LAN
- To allow clients to find the AP easily, the AP periodically broadcasts beacons, announcing its (SSID) Service Set Identifier, data rates, and other WLAN information.
- SSID is a naming scheme for WLANs to allow an administrator to group WLAN devices together.
- To discover APs, clients will scan all channels and listen for the beacons from the AP(s). By default, the client will associate itself with the AP that has the strongest signal.
- When the client associates itself with the AP, it sends the SSID, its MAC address, and any other security information that the AP might require based on the authentication method configured on the two devices.
- Once connected, the client periodically monitors the signal strength of the AP to which it is connected.
- If the signal strength becomes too low, the client will repeat the scanning process to discover an AP with a stronger signal. This process is commonly called roaming.
SSID and MAC Address Filtering
When implementing SSIDs, the AP and client must use the same SSID value to authenticate. By default, the access point broadcasts the SSID value, advertising its presence, basically allowing anyone access to the AP. Originally, to prevent rogue devices from accessing the AP, the administrator would turn off the SSID broadcast function on the AP, commonly called SSID cloaking. To allow a client to learn the SSID value of the AP, the client would send a null string value in the SSID field of the 802.11 frame and the AP would respond; of course, this defeats the security measure since through this query process, a rogue device could repeat the same process and learn the SSID value.
Therefore, the APs were commonly configured to filter traffic based on MAC addresses. The administrator would configure a list of MAC addresses in a security table on the AP, listing those devices allowed access; however, the problem with this solution is that MAC addresses can be seen in clear-text in the airwaves. A rogue device can easily sniff the airwaves, see the valid MAC addresses, and change its MAC address to match one of the valid ones.
This is called MAC address spoofing.
WEP
WEP (Wired Equivalent Privacy) was first security solutions for WLANs that employed encryption. WEP uses a static 64-bit key, where the key is 40 bits long, and a 24-bit initialization vector (IV) is used. IV is sent in clear-text. Because WEP uses RC4 as an encryption algorithm and the IV is sent in clear-text, WEP can be broken. To alleviate this problem, the key was extended to 104 bits with the IV value. However, either variation can easily be broken in minutes on laptops and computers produced today.
802.1x EAP
The Extensible Authentication Protocol (EAP) is a layer 2 process that allows a wireless client to authenticate to the network. There are two varieties of EAP: one for wireless and one for LAN connections, commonly called EAP over LAN (EAPoL).
One of the concerns in wireless is allowing a WLAN client to communicate to devices behind an AP. Three standards define this process: EAP, 802.1x, and Remote Authentication Dial In User Service (RADIUS). EAP defines a standard way of encapsulating authentication information, such as a username and password or a digital certificate that the AP can use to authenticate the user.802.1x and RADIUS define how to packetize the EAP information to move it across the network.
WPA

Wi-Fi Protected Access (WPA) was designed by the Wi-Fi Alliance as a temporary security solution to provide for the use of 802.1x and enhancements in the use of WEP until the 802.11i standard would be ratified. WPA can operate in two modes: personal and enterprise mode. Personal mode was designed for home or SOHO usage. A pre-shared key is used for authentication, requiring you to configure the same key on the clients and the AP. With this mode, no authentication server is necessary as it is in the official 802.1 x standards. Enterprise mode is meant for large companies, where an authentication server will centralize the authentication credentials of the clients.
WPA2
WPA2 is the IEEE 802.11i implementation from the Wi-Fi Alliance. Instead of using WEP, which uses the weak RC4 encryption algorithm, the much more secure Advanced Encryption Standard (AES)–counter mode CBC-MAC Protocol (CCMP) algorithm is used.
Infrared
Infrared (IR) radiation is electromagnetic radiation of a wavelength longer than that of visible light, but shorter than that of microwave radiation. The name means 'below red' (from the Latin infra, 'below'), red being the color of visible light of longest wavelength.
Bluetooth
Wireless Data Device Network & Wireless Cards Drivers
Is an industrial specification for wireless personal area networks (PANs). Bluetooth provides a way to connect and exchange information between devices like personal digital assistants (PDAs), mobile phones, laptops, PCs, printers and digital cameras via a secure, low-cost, globally available short range radio frequency.
FHSS
Frequency-hopping spread spectrum is a spread-spectrum method of transmitting radio signals by rapidly switching a carrier among many frequency channels, using a pseudorandom sequence known to both transmitter and receiver. Spread-spectrum transmission offers these advantages over a fixed-frequency transmission:
- Highly resistant to noise and interference.
- Signals are difficult to intercept. A Frequency-Hop spread-spectrum signal sounds like a momentary noise burst or simply an increase in the background noise for short Frequency-Hop codes on any narrowband receiver except a Frequency-Hop spread-spectrum receiver using the exact same channel sequence as was used by the transmitter.
- Transmissions can share a frequency band with many types of conventional transmissions with minimal interference. As a result, bandwidth can be utilized more efficiently.
DSSS
direct-sequence spread spectrum is a modulation technique where the transmitted signal takes up more bandwidth than the information signal that is being modulated, which is the reason that it is called spread spectrum. Direct Sequence Spread Spectrum (DSSS)uses one channel to send data across all frequencies within that channel. Complementary Code Keying (CCK) is a method for encoding transmissions for higher data rates, such as 5.5 and 11 Mbps, but it still allows backward compatibility with the original 802.11 standard, which supports only 1 and 2 Mbps speeds. 802.11b and 802.11g support this transmission method.
Comparison of DSSS and Frequency Hopped SS
DSSS
- Flexible support of variable data rates
- High capacity is possible with enhancements (interference cancellation, adaptive antenna, etc.)
- Suffers from near-far effect
FHSS
- Suitable for ad hoc networks (no near-far problem)
- Robust to interference
- Limited data rate
OFDM
Orthogonal frequency-division multiplexing, also called discrete multitone modulation (DMT), is a transmission technique based upon the idea of frequency-division multiplexing (FDM). OFDM (Orthogonal Frequency Division Multiplexing) increases data rates by using a spread spectrum: modulation. 802.11a and 802.11g support this transmission method.
- Used in some wireless LAN applications, including WiMAX and IEEE 802.11a/g
- Used in many communications systems such as: ADSL, Wireless LAN, Digital audio broadcasting.
MIMO (Multiple Input Multiple Output)
MIMO (Multiple Input Multiple Output) transmission, which uses DSSS and/or OFDM by spreading its signal across 14 overlapping channels at 5 MHz intervals. 802.11n uses it. Use of 802.11n requires multiple antennas.
| 802.11a | 802.11b | 802.11g | 802.11n | |
| Data Rate | 54 Mbps | 11 Mbps | 54 Mbps | 248 Mbps (with 2×2 antennas) |
| Throughput | 23 Mbps | 4.3 Mbps | 19 Mbps | 74 Mbps |
| Frequency | 5 GHz | 2.4 GHz | 2.4 GHz | 2.4 and/or 5 GHz |
| Compatibility | None | With 802.11g and the original 802.11 | With 802.11b | 802.11a, b, and g |
| Range (meters) | 35–120 | 38–140 | 38–140 | 70–250 |
| Number of Channels | 3 | Up to 23 | 3 | 14 |
| Transmission | OFDM | DSSS | DSSS/OFDM | MIMO |
Radio Frequency Transmission Factors
Radio frequencies (RF) are generated by antennas that propagate the waves into the air. Antennas fall under two different categories:
- Directional
- Omni-directional
Directional Directional antennas are commonly used in point-to-point configurations (connecting two distant buildings), and sometimes point-to-multipoint (connecting two WLANs). An example of a directional antenna is a Yagi antenna: this antenna allows you to adjust the direction and focus of the signal to intensify your range/reach.
Wireless Data Device Network & Wireless Cards Drivers
Omni-directional Omni-directional antennas are used in point-to-multipoint configurations, where they distribute the wireless signal to other computers or devices in your WLAN. An access point would use an omni-directional antenna. These antennas can also be used for point-to-point connections, but they lack the distance that directional antennas supply
Three main factors influence signal distortion:
- Absorption Objects that absorb the RF waves, such as walls, ceilings, and floors
- Scattering Objects that disperse the RF waves, such as rough plaster on a wall, carpet on the floor, or drop-down ceiling tiles
- Reflection Objects that reflect the RF waves, such as metal and glass
Responsible body
The International Telecommunication Union-Radio Communication Sector (ITU-R) is responsible for managing the radio frequency (RF) spectrum and satellite orbits for wireless communications: its main purpose is to provide for cooperation and coexistence of standards and implementations across country boundaries.
Two standards bodies are primarily responsible for implementing WLANs:
- The Institute of Electrical and Electronic Engineers (IEEE)
- The Wi-Fi Alliance.
IEEE Defines the mechanical process of how WLANs are implemented in the 802.11 standards so that vendors can create compatible products.
The Wi-Fi Alliance Basically certifies companies by ensuring that their products follow the 802.11 standards, thus allowing customers to buy WLAN products from different vendors without having to be concerned about any compatibility issues.
Frequencies bands:
WLANs use three unlicensed bands:
- 900 MHz Used by older cordless phones
- 2.4 GHz Used by newer cordless phones, WLANs, Bluetooth, microwaves, and other devices
- 5 GHz Used by the newest models of cordless phones and WLAN devices
900 MHz and 2.4 GHz frequencies are referred to as the Industrial, Scientific, and Medical (ISM) bands.
5 GHz frequency the Unlicensed National Information Infrastructure (UNII) band.
Unlicensed bands are still regulated by governments, which might define restrictions in their usage.
A hertz (Hz) is a unit of frequency that measures the change in a state or cycle in a wave (sound or radio) or alternating current (electricity) during 1 second.
802.11g
Suffers from the same interference as 802.11b in the already crowded 2.4 GHz range. Devices operating in this range include microwave ovens, Bluetooth devices, and cordless telephones. Since the 2.4 GHz band is heavily used, using the 5 GHz band gives 802.11a the advantage of less interference. However, this high carrier frequency also brings disadvantages. It restricts the use of 802.11a to almost line of sight, necessitating the use of more access points; it also means that 802.11a cannot penetrate as far as 802.11b since it is absorbed more readily, other things (such as power) being equal.
802.11a
Transmits radio signals in the frequency range above 5 GHz. This range is 'regulated,' meaning that 802.11a gear utilizes frequencies not used by other commercial wireless products like cordless phones. In contrast, 802.11b utilizes frequencies in the unregulated 2.4 GHz range and encounters much more radio interference from other devices.
IEEE 802.11a / IEEE 802.11h
This is also a physical layer enhancement. IEEE 802.11a provides significantly higher performance than 802.11b, at 54 Mbps. Unlike 802.11b, the 802.11a standard operates within the frequency range of 5.47 to 5.725 GHz and is not subject to the same interference from other commercial electronic products. This higher frequency band allows significantly higher speeds of communication over the 2.4 GHz range.
802.11g APs are backward compatible with 802.11b APs. This backward compatibility with 802.11b is handled through the MAC layer, not the physical layer. On the negative side, because 802.11g operates at the same frequency as 802.11b, it is subject to the same interferences from electronic devices such as cordless phones. Since the standard’s approval in June 2003, 802.11g products are gaining momentum and will most likely become as widespread as 802.11b products. Table II-1 displays basic 802.11b/a/g characteristics.
The common range of operation for 802.11b is 150 feet for a floor divided into individual offices by concrete or sheet-rock, about 300 feet in semi-open indoor spaces such as offices partitioned into individual workspaces, and about 1000 feet in large open indoor areas. Disadvantages of 802.11b include interference from electronic products such as cordless phones and microwave ovens.
Range
The layout of your building can reduce the range.
- A lot of concrete walls can reduce your range.
- The size of the antenna and the placement greatly affect the range of their signals
- The weather and amount of water vapor in the air can affect your signals strength
Speed
- The layout of your building can reduce the speed
- The size of the antenna and its signal can affect your speed
- The weather and amount of water vapor can weaken the signal and affect your speed
